The Internet Archive, a digital repository tasked with preserving the world’s knowledge, recently fell victim to a DDoS attack. This assault on the cornerstone of digital preservation raises several questions about the motives behind such acts and the broader implications for online security. More importantly, it serves as a stark reminder of the vulnerabilities that even the most benevolent online entities face in today’s interconnected world.
Many commentators, as seen on platforms discussing the incident, expressed their confusion and frustration over the seemingly pointless attack on a digital library. Commenting on the act, several users noted the absurdity of attacking a repository of knowledge that benefits millions worldwide. ‘My thoughts exactly’, one user echoed, highlighting the senselessness of targeting an institution primarily focused on public good. Such sentiment resonates with many who view libraries, whether physical or digital, as sanctuaries of knowledge and progress.
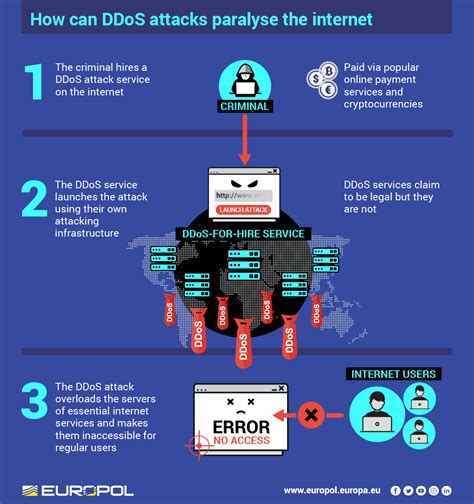
Explorations into the potential motives behind the DDoS attack offered a variety of perspectives. One prevailing theory is the concept of showcasing capabilities. As one commenter pointed out, such attacks may serve as demonstrations of capacity by those offering DDoS-for-hire services. This could be seen as a form of dark advertising, where disrupting a well-known site like the Internet Archive becomes proof of effectiveness for potential clients. This view is buttressed by the historical context of attacks on similarly non-malignant targets for the purpose of flexing digital muscle.
Another user brought up an interesting point about ideology, or rather, the seeming lack of it. There’s a palpable irony in attackers, who often rely on the same internet freedoms and resources they seek to disrupt. It’s counterintuitive and speaks to a larger issue within the hacker community’s ethics, or lack thereof. This raises questions about the evolution of hacking from noble causes, such as activism and whistleblowing, to mere vandalism devoid of any altruistic purpose.
The financial underpinnings behind such attacks cannot be ignored. The cost and ease of launching a DDoS attack have drastically decreased, making it accessible even to those with limited resources. Commenters pointed out that with services available for as low as $14.99 a month, almost anyone can disrupt online services at will. This democratization of cyber-attacks exemplifies the dual-edged nature of technological advancements—facilitating both beneficial and malevolent activities.
The role of companies like Cloudflare has also been brought into focus during this discourse. While Cloudflare offers protection against such attacks, there’s a growing concern about their ethical stance. Several comments highlighted a perceived conflict of interest, whereby Cloudflare’s services are used by both DDoS mitigation clients and DDoS operators. Although Cloudflare often justifies its actions under the guise of maintaining content neutrality, the overlap between protection and facilitation is troubling to many in the cybersecurity community.
Ultimately, the attack on the Internet Archive underscores the fragility of even the most well-intentioned digital projects. In a digital age where information is power, ensuring the security and accessibility of repositories like the Internet Archive is more crucial than ever. As the defenders of free and open access to knowledge, institutions must regularly adapt to evolving threats. This incident serves as a call to action for enhanced measures in cybersecurity protocols and a rallying cry for the broader community to support and protect digital heritage.
As digital stewards, we must acknowledge these challenges and work collaboratively to mitigate them. One potential way forward is leveraging open-source technologies for DDoS protection. Platforms such as HAProxy offer configurations for application-layer DDoS mitigation. A basic setup might look like this:
global
log /dev/log local0
maxconn 4000
user haproxy
group haproxy
daemon
defaults
log global
mode http
option httplog
timeout connect 5s
timeout client 50s
timeout server 50s
frontend http_front
bind *:80
default_backend http_back
backend http_back
balance roundrobin
server server1 127.0.0.1:8080 check
Such integrations can offer a level of resilience, ensuring that digital repositories can withstand attacks and continue to serve the public. Additionally, fostering a community ethos around supporting and safeguarding these digital assets can further strengthen their defenses. By doing so, we uphold a collective responsibility to preserve and protect access to information—a bedrock principle in the digital age.

Leave a Reply