Tag: Authentication
-
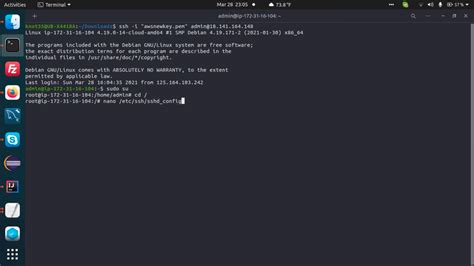
Revamping Root Access: Could SSH Replace Sudo?
Root access in Unix-like systems has always been a hot topic of debate among system administrators and security professionals. Traditionally, the ‘sudo’ command has been the go-to tool for gaining superuser permissions without logging in as root. However, a recent thought-provoking experiment suggests using SSH (Secure Shell) as an alternative method to obtain root-level permissions.…
-

How Deepfake Scams Are Shaking up the Financial Industry
The recent $25M deepfake scam involving British engineering giant Arup has brought to light the vulnerabilities in financial transactions amidst advancements in artificial intelligence technology. Comments from users reflect a mix of concern, skepticism, and proposed solutions to combat such fraudulent activities. Amidst the discussions, the consensus seems to lean towards reinforcing authentication mechanisms and…
-

Unveiling the Complexity of Identity Theft and Bank Responsibilities
Identity theft is a multifaceted issue that raises questions about the boundaries of responsibility between customers and banks. The comments on a recent article shed light on the complexities surrounding this topic. One user shared a personal experience of winning Apple gift cards, being scammed, and eventually unraveling the mystery by creatively tracking down the…
-

Understanding Identity Theft and the Responsiblitiy of Banks
Identity theft remains a pervasive issue in the digital age, as showcased in the experiences shared by individuals grappling with fraudulent activities. Amidst the narratives of financial loss and painstaking investigations, the underlying theme of accountability emerges prominently. While victims recount their arduous journeys to reclaim stolen funds and uncover the perpetrators, questions surrounding the…
-

Decoding the Maze of Passkey Implementations and User Experiences
The introduction of passkeys marks a significant evolution in digital authentication, aiming to enhance security while simplifying the user experience. As passkeys begin to replace traditional passwords, they bring about a new set of challenges and considerations for developers and users. The nuances of implementing passkey-based systems are not trivial, and the practical experiences shared…
-

Tumadh ar Stack: Rogha Eile Auth Dúshlánach do Chláraitheoirí
Sa ré dhigiteach seo, tá éileamh níos mó ná riamh ar uirlisí bainistíochta úsáideoirí agus fíordheimhniú a chuirtear i bhfeidhm go tapa agus go héifeachtach. Cuireann Stack, taiscéalaí nua i réimse na mbogearraí foinse oscailte, roghanna suimiúla ar fáil do fhorbróirí atá ag iarraidh smacht iomlán a bheith acu ar a gcórais fíordheimhnithe gan cur…
-

Delving Into Stack: A Fresh Approach to Authentication and User Management
Releasing a new authentication and user management tool into the tech ecosystem, Stack introduces a blend of flexibility and openness that seeks to streamline the development process for software engineers. Particularly in startups, where time and resources are often tight, Stack promises a straightforward integration with existing systems, allowing developers to implement robust authentication processes…
-

L-Era l-Ġdida tal-Awtentikazzjoni: Stack Jagħti Soluzzjoni Miftuħa u Adattabbli
Il-ħolqien ta’ Stack, pjattaforma għall-awtentikazzjoni u l-ġestjoni ta’ l-utenti, huwa mument definittiv għal żviluppaturi li jfittxu li jimplimentaw soluzzjonijiet effiċjenti u adattabbli fil-proġetti tagħhom. Is-simpliċità fl-integrazzjoni u l-adattabbiltà mal-ħtiġijiet attwali tad-disinn jidhru bħala l-fatturi ewlenin wara dan il-proġett. L-introduzzjoni ta’ komponenti bħal u li jadattaw awtomatikament mal-iskemi tal-kulur u d-disinni tal-utenti hija innovazzjoni fid-dinja tal-applikazzjonijiet…
-
Stack: A New Open-Source Contender in the Authentication Space
In the ever-evolving landscape of software development, the introduction of Stack marks a significant development in the way authentication systems are incorporated into applications. Launched with the promise of easing the burdensome process of user management and authentication, Stack positions itself as not merely another tool but as a game-changer in rapid deployment. With features…

